Identify your Risks before others do
Security is a holistic procedure that needs to start at the beginning of the design phase of the software.


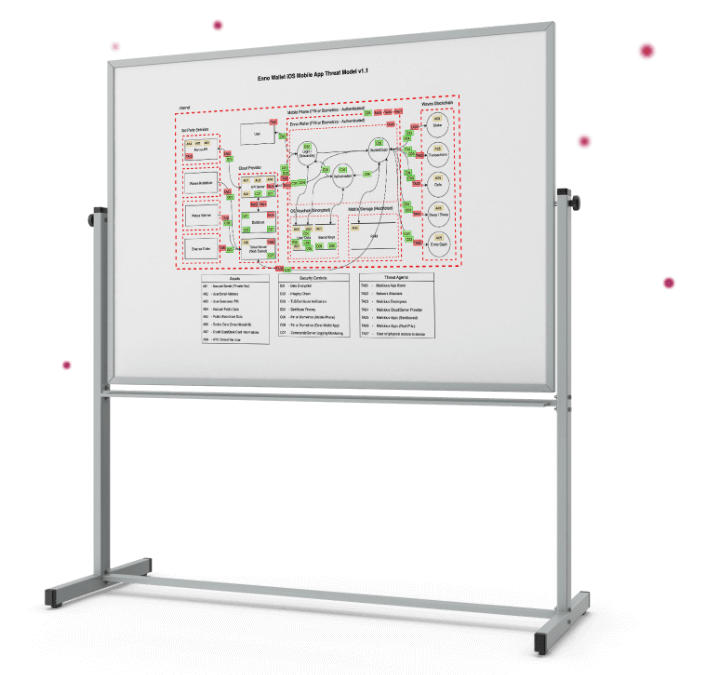
Threat Model is
the best way
to identify risks
Threat Modeling is a structured methodology that is frequently used in the field of security. The objective is to determine the architecture, processes, and complex processes of the software and to identify its security requirements, threats, and potential vulnerabilities.
Not only this, they are added to this diagram after determining the priorities of the threats and weaknesses that may occur in these works and determining the security measures/controls that are to be applied for them.
Industry Standards Combined
with The Industry Experience
At Enno Wallet, we use the STRIDE method, one of the widespread methods, Threat Modeling Manifesto, and OWASP as we structure the Threat Model.
Meanwhile, we not only use the best methodologies but also apply our security measures; we also take into account all the security incidents and known weaknesses that blockchain, cryptocurrency exchange, and crypto wallet products have experienced so far.

What is Next
See Other Security Precautions
Enno Wallet has much more to offer about security.
Please be sure to check all other precautions.
Keycard
Store your private seed phrases in Keycard and maximize your Web3 account security. This means that your Enno Wallet is now a hardware wallet with Keycard. Sync your keycard with your Web3 account, export your seed phrase to the card and enjoy your new hardware wallet.
Seed Phrase
Enno Wallet is a non-custodial (self-custodial) DeFi Wallet. It is only your account and your wallet. Enno Wallet uses seed phrases, which is the industry standard for creating private keys.
Passcode
We encrypt core wallet data using bank-grade encryption after you set a passcode. Enno Wallet combines the security best practices with the best user experience.
